Wildix Security and Products Overview
This document provides information on built-in security features of the Wildix system and Wildix services description.
Updated: September 2023
Permalink: https://wildix.atlassian.net/wiki/x/vQFmBQ
Security is a top priority for Wildix and all the security features are built-in inside the product, which means the Wildix System is Secure By Design.
Security measures in place
We support the following security and encryption protocols and reporting tools:
Single Sign-On with Active Directory, Google, Microsoft Office 365
2 Factor Authentication when using Google, Microsoft Office 365 Single Sign-On
SHA-512 hashing + salt, for storing user passwords securely
TLS encryption of HTTPS traffic to the PBX, screen sharing sessions, Wizyconf conferences
SIP TLS - SIP signalling over TLS
SRTP - SDES-AES 128 encryption of voice / audio, including Wizyconf conferences
DTLS-SRTP - TLS encryption of voice / audio, including Wizyconf conferences
VPN AES encrypted traffic between PBXs
LDAP via TLS
SMTP / IMAP / POP3 connections over TLS
SSH console access
Intrusion detection over all services managed by the PBX (SIP / RTP / DNS proxy / NTP / Web)
DoS protection over all services managed by the PBX (SIP / RTP / DNS proxy / NTP / Web)
SIP SBC built in
Protection against cross-site request forgery (CSRF) attacks
Requirement for secure passwords
Support for Zabbix monitoring
Report of intrusion attempts detected within the System
All these security measures are enabled by default on all Wildix Phones and Media Gateways connected to the system. All Wildix Phones and Media Gateways cannot be accessed by using Master Passwords.
Wildix Cloud and ISO 27001, 22301 compliance
Wildix Cloud network is powered by Amazon Web Services, whose data centers undergo ISO 27001 and ISO 22301 audits (for more information, you can refer to this page). These data centers share hosted facilities space with the world’s largest Internet companies. The geographic diversity of these locations act as an additional safeguard which minimizes the risk of service interruption due to natural disasters.
Security standards
1. Authentication
The solution supports SAML2 and OpenID.
Exclusive SSO authentication; no other authentication methods (login/password, etc.) are authorized to access end-user data. SSO via an external identity provider can be forced and password authentication blocked.
2. Traffic Encryption
- Certificate used for identity of hosting asset is valid, using at least SHA256 key exchange mechanism and having any intermediate certificate within the certification chain valid and respecting the same above criteria.
- Certificates for identity of hosting assets comply with Certificate Transparency standard (https://www.certificate-transparency.org). The certificate used on systems can be freely validated at any time as requested by clients.
- The solution is accessible through HTTPS only with strong encryption protocol implementation: Vulnerable TLS 1.0 & 1.1, SSL v2 & v3 protocols are disabled. Only TLS 1.2 is allowed as a security protocol and all previous protocols are disabled by default.
- Protocol downgrade attacks are mitigated using the TLS_FALLBACK_SCSV mechanism.
- Cipher suites in encrypted traffic do not use: null encryption, obsolete cipher MD5, RC4, DHE, CBC and DES3. Additionally, the Wildix system can be switched between security mods in order to support outdated devices, while still using only modern ciphers.
- Perfect Forward Secrecy (PFS) Support: The solution supports ECDHE or AES suites in order to enable Forward Secrecy with modern web browsers.
- All cipher suite combinations that do not support Perfect Forward Secrecy (such as RSA) are banned.
- Cipher suites configuration are sorted from the strongest to the lowest.
- Solution supports HTTP Strict Transport Security (HSTS) for Web Servers to prevent Man-In-The-Middle Attacks.
- For security and performance reasons, each Wildix system uses sub-domains.
3. Secure Cookies
Wildix makes reasonable efforts to prevent cookie/session leaks, such as centralized CSRF protection and similar proactive measures.
4. Implementation of best practices to avoid security risks
Wildix follows OWASP recommended practices, performs penetration testing and educates employees. More details can be provided after signing an NDA.
5. Mitigations Against CPU Speculative Execution Attack Methods
Mechanisms are in place to protect against CVE-2017-5754 - Meltdown, CVE-2017-5753 - Spectre 1, CVE-2017-5715 - Spectre 2 (CVE-2017-5753, CVE-2017-5715, and CVE-2017-5754). Wildix implements mitigations of both programmatic (kernel updates/modifications) and hardware (CPUs used are not affected) varieties.
Hosting services description
1. Data location:
You have possibility to choose the desired location
2. Security policy and tools:
Complex password requirements, non-vulnerable encryption methods, certificate checks, WebRTC security, GDPR Security compliance, physical database access protections, and security vulnerabilities are patched as quickly as possible in accordance with OWASP risk rating methodology
3. Intrusion Detection policy and tools:
Intrusion detection over all services managed by the PBX (SIP / RTP / DNS proxy / NTP / Web), penetration tests are performed yearly and security reports summaries are released on request after signing an NDA to existing customers.
4. Disaster Recovery Plan (DRP) description, recovery time objective (RTO) and recovery point objective (RPO):
Typical methodology is to recover and/or rollback from backup, which entails a maximum downtime period of 15 minutes. Process also makes use of site monitoring and SRE to start the procedure proactively if needed.
5. Architecture to ensure the service availability and data integrity:
Failover protection using multiple AWS server sites, or roll over from backup.
Service availability
The availability commitment for the WILDIX services is 99.98%, disregarding any scheduled periods of unavailability for preventive maintenance notified in advance. The availability of the WILDIX services is calculated daily and it’s available here: https://statuspage.wildix.com/. It measures whether the technical interfaces are operational and not user perceptions.
Overview of Wildix Products
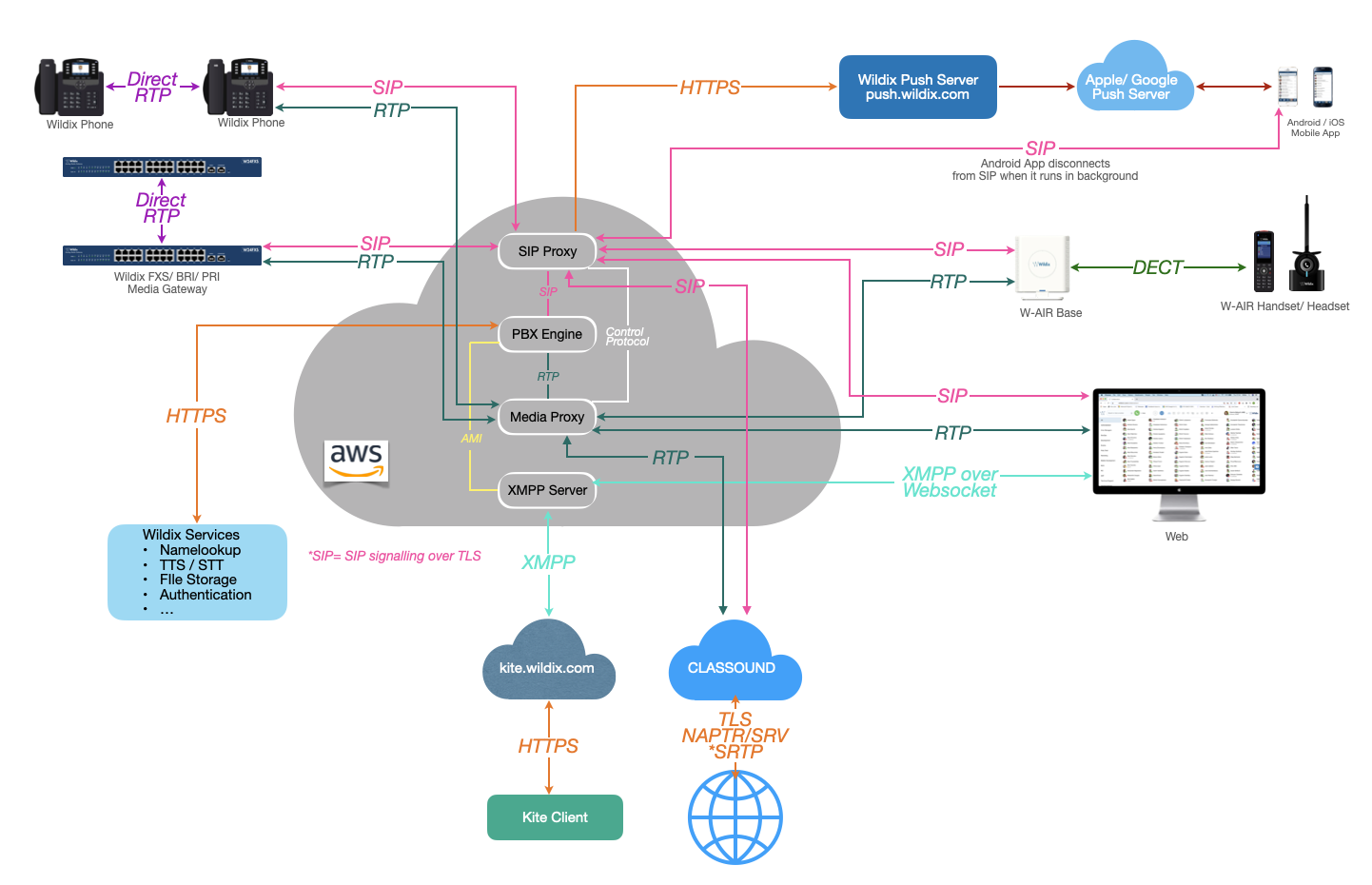
WMS Structure
The scheme below displays the structure of WMS (Wildix Management System):
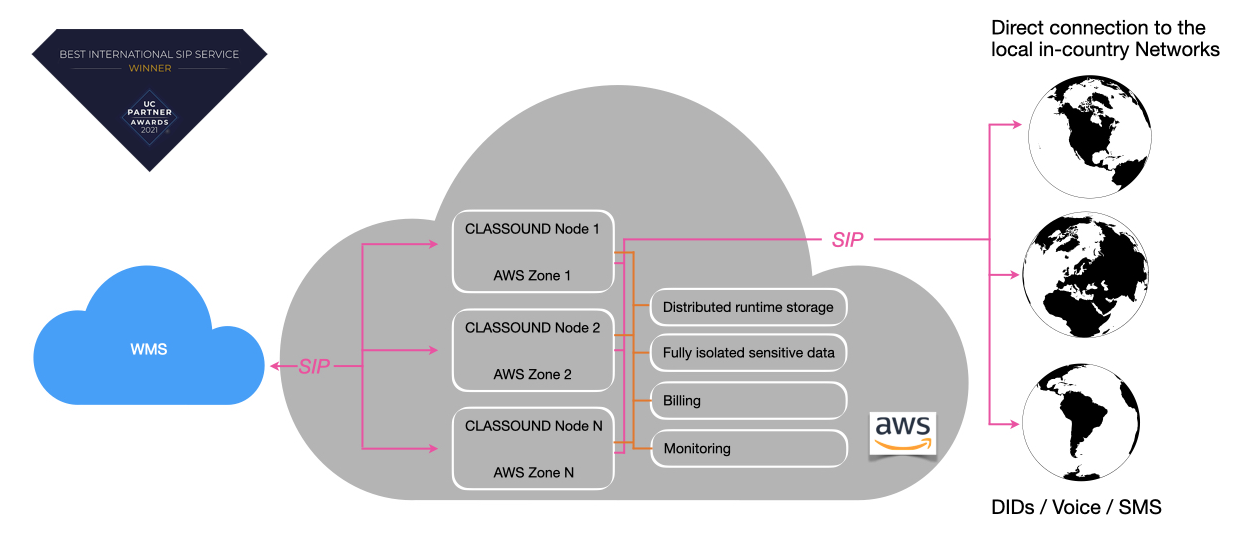
CLASSOUND
CLASSOUND is a fully Cloud-based service that goes beyond SIP trunks in its capabilities. Using CLASSOUND, companies can enjoy the full capabilities of a communications system with global coverage, combined with the security and maintenance they’d expect from a modern enterprise-grade VoIP system.
Scheme of the CLASSOUND service:
Note: "WMS" here implies the scheme provided in the section WMS Structure.
Reliability:
- 100% Cloud-based
- Global presence with AWS Availability Zones
- 99.98% availability provided with NAPTR/SRV
- Call failure rate 0,2%
- Call set-up time 1.4 sec
- Redundancy
- 24/7 Monitoring
Security:
- Isolated structure available only for Wildix Ecosystem
- Network security
- Direct connections to Local Country Networks
Global Coverage:
- 200+ Countries and Territories for Outbound calling
- 100+ Countries Local DIDs coverage
- Landline and Mobile DIDs
- Voice and SMS
CLASSOUND Service meets:
- Local Service Registration and Authorisation requirements
- General Data Protection Regulation requirements
- Emergency Service regulation requirements
Voice technologies:
- SIP with G.729, G.711, OPUS, T.38
- TLS
- SRTP - coming soon
Additional features:
- Instant Virtual Porting
- Bulk SMS sending
- Forwarding
- Bult-in Trunk setup
- Failover
- Filtering/Blacklists/Anti-spoofing
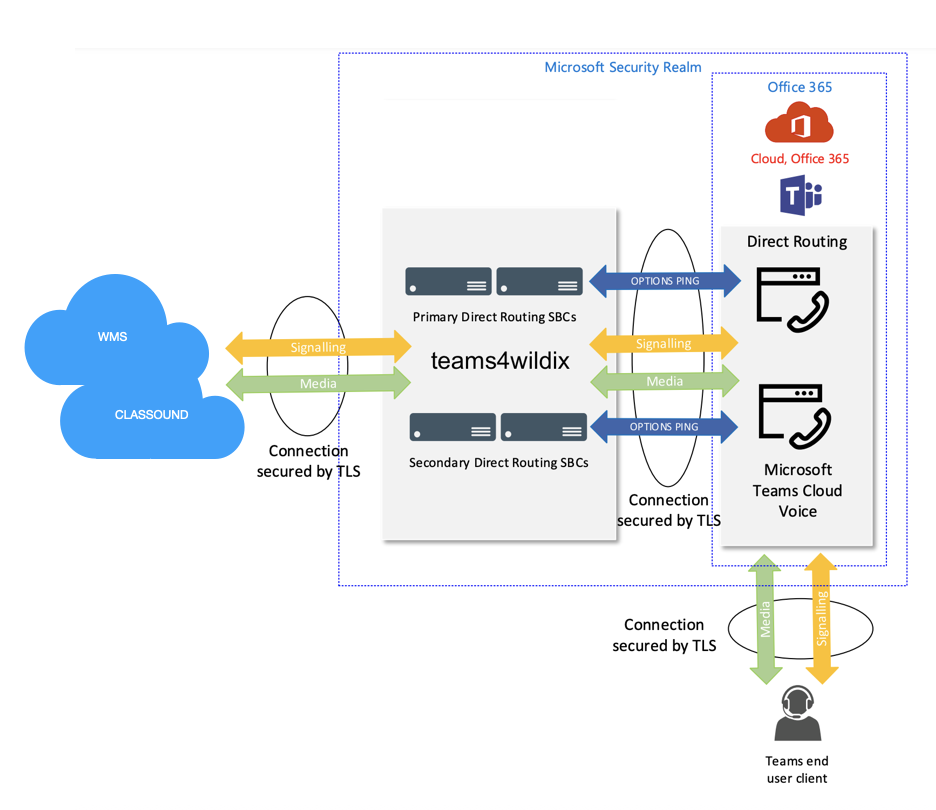
teams4Wildix
With Wildix, you get a Microsoft Teams PBX integration that gives you all the telephony features a growing business needs to simplify communication and deliver more to the bottom line.
Wildix offers 2 modes of Integration usage.
Mode 1. Collaboration App: it provides access to all advanced features by Wildix.
Mode 2. MS Phone System: besides the advantages of Mode 1, it allows MS Teams users to place and receive calls using Teams Dialpad (Calls tab of the MS Teams interface).
teams4Wildix service integration scheme:
teams4Wildix security:
- All call legs can be secured by TLS encryption. TLS 1.2 or later is supported
- Customer data held in the Microsoft security realm for both Teams and teams4Wildix
- Teams users connect to the nearest Microsoft network POP
- The Microsoft network carries the voice traffic for nearly the entire journey
- Through teams4Wildix node optimisation, traffic will step-off the Microsoft network near to the PBX or Trunk
teams4Wildix features:
- Support for Teams in the browser version and native app
- Single sign-on with Microsoft 365 (Office 365)
- Inbound and outbound calls (internally and externally) within Teams
- Call control of any Wildix devices assigned to the user’s account, including desk phones, DECT
- Embedded SIP trunk that enables long-distance calls to 200+ countries
- Integrated Fax and SMS server
- Robust and reliable phone system that offers all the advanced telephony features
- No complicated setup and added costs; calling to and from Teams is available out of the box