How to block spoofed calls received via CLASSOUND
This Article explains how to block spoofed calls received via CLASSOUND using STIR/SHAKEN technology.
Created: September 2021
Permalink: https://wildix.atlassian.net/wiki/x/ixfOAQ
For now, the feature is available only for the US DIDs. The support for Canadian DiDs will be added in November 2021.
Introduction
Thanks to the STIR/SHAKEN Inbound Verification (VERSTAT) feature, it is possible to authenticate and verify the true caller identity behind a given phone call and block such spoofing calls so they don't reach customers in the first place.
How STIR/SHAKEN works
STIR/SHAKEN uses digital certificates, based on common public key cryptography techniques, to ensure the calling number of a telephone call is secure. In simple terms, each telephone service provider obtains their digital certificate from a certificate authority who is trusted by other telephone service providers.
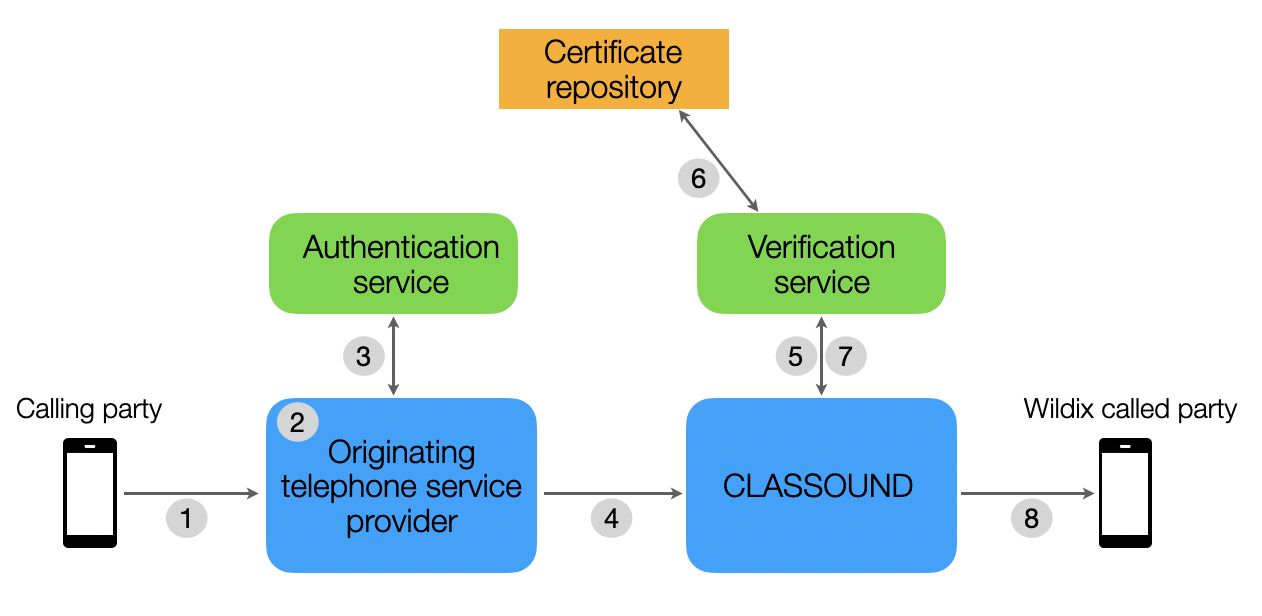
STIR/SHAKEN call flow diagram illustrates how the technology works:
1. A SIP INVITE is received by the originating telephone service provider
2. The originating telephone service provider checks the call source and calling number to determine how to attest for the validity of the calling number
- Full or A Attestation - the service provider authenticates the calling party and they are authorized to use the calling number. An example of this case is a subscriber registered with the originating telephone service provider’s softswitch
- Partial or B Attestation - the service provider authenticates the call origination, but cannot verify the call source is authorized to use the calling number. An example of this use case is a telephone number behind a PBX
- Gateway or C Attestation - the service provider authenticates from where it received the call, but cannot authenticate the call source. An example of this case would be a call received from an international gateway
3. The originating telephone service provider uses the authentication service to create a SIP Identity header. The authentication service could be a third-party service hosted in the cloud a software application integrated with the telephone service provider’s softswitch or Session Border Controller (SBC). The SIP Identity header contains the following data:
- Calling number
- Called number(s)
- Current timestamp
- Attestation level
- Origination identifier
4. The SIP INVITE with the SIP Identity header is sent to CLASSOUND
5. The SIP INVITE with Identity header is passed to the verification service
6. The verification service obtains the digital certificate of the originating telephone service provider from the public certificate repository and begins a multi-step verification process
If all verification steps are successful, then the calling number has not been spoofed
- The SIP Identity header is base64 URL decoded and the details are compared to the SIP INVITE message
- The public key of the certificate is used to verify the SIP Identity header signature
- The certificate chain of trust is verified
7. The verification service returns the results to CLASSOUND
8. The call is completed to the called party
Dialplan Configuration
For visualize the Attestation, Caller name will be changed and saved to CDR-View in a new format.
The set up STIR/SHAKEN for CLASSOUND calls, proceed with the following steps:
- Go to WMS Dialplan -> Dialplan rules
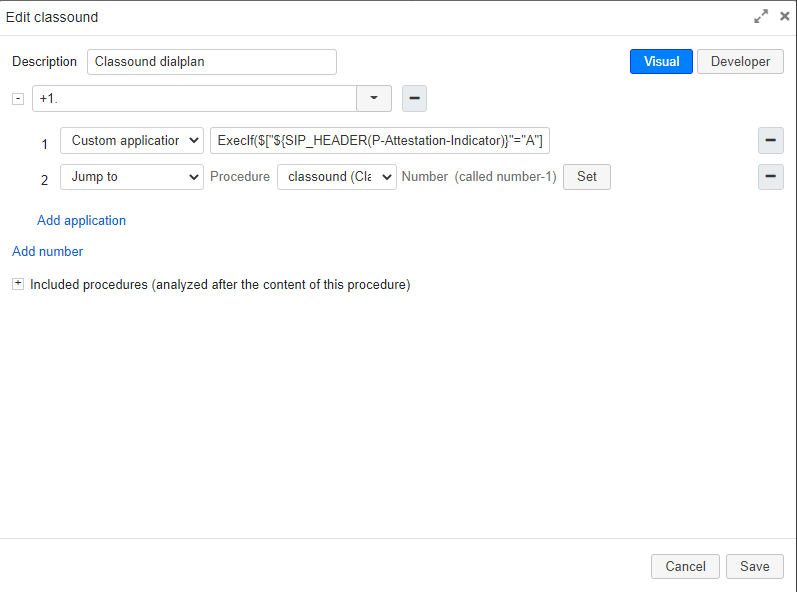
- Select classound Dialplan procedure, add a called number, for example, +1., and add the following applications:
- Custom application -> ExecIf($["${SIP_HEADER(P-Attestation-Indicator)}"="A"]?Set(CALLERID(name)=verified ${CALLERID(name)}):ExecIf($["${SIP_HEADER(P-Attestation-Indicator)}"="B"]?Set(CALLERID(name)=verified ${CALLERID(name)}):Set(CALLERID(name)=unknown ${CALLERID(name)})))
- Jump to -> classound -> set( strip plus from called number for example)
In this case, the Attestation levels A and B are determined as verified, and level C - as unknown.
You can customize the verification levels verified and unknown, just edit the variable according to your needs:
- ExecIf($["${SIP_HEADER(P-Attestation-Indicator)}"="A"]?Set(CALLERID(name)=verified ${CALLERID(name)}):ExecIf($["${SIP_HEADER(P-Attestation-Indicator)}"="B"]?Set(CALLERID(name)=verified ${CALLERID(name)}):Set(CALLERID(name)=unknown ${CALLERID(name)})))
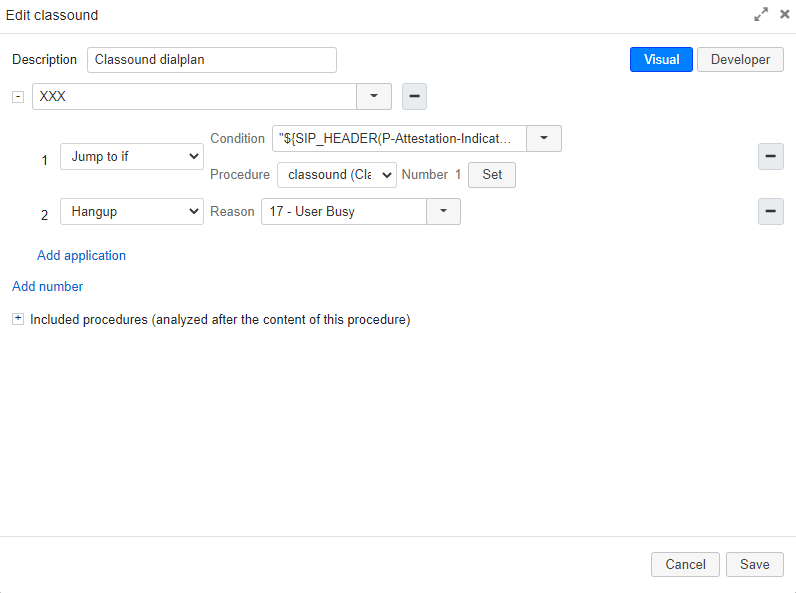
To block calls based on C indicator, use "${SIP_HEADER(P-Attestation-Indicator)} variable.
For example, add these Dialplan applications:
- Jump to if -> Condition "${SIP_HEADER(P-Attestation-Indicator)}"="C"
- Hang-up -> reason (User Busy)